Welcome to /mlpol/ weary travellers. In this thread I will collect what I can find about the 4chan hack and try to provide a base camp for those lost 4nons that have managed to find their way here. Feel free to add anything you know or swap stories as well. The following is roughly gathered to ensure it is saved.
kiwifarms threads: https://kiwifarms.st/threads/4chan.37222/page-421#post-21099990
janny lists
https://kiwifarms.st/threads/4chan.37222/page-474#post-21102637
yotsuba sauce
https://kiwifarms.st/threads/4chan.37222/page-475#post-21102680
Hiro on twitter: https://xcancel.com/4chan/status/1912242601102844078
https://x.com/4chan/status/1912242601102844078
Commit messages on 4chan repo:
https://files.catbox.moe/yypkoa.txt
Potential information sources you may keep an eye on:
4chan's IRC channel on Rizon
Hiro's 4chan twitter: https://x.com/4chan
Sun article tracking the incident: https://www.the-sun.com/tech/14029069/4chan-down-updates-controversial-website-hacking/
Sinister/pol/: https://leftypol.org/
Know your meme article: https://knowyourmeme.com/memes/events/april-2025-4chan-sharty-hack-and-janitor-email-leak
Sharty: https://www.soyjak.st/news/thread/4104.html
4chan itself of course: https://boards.4chan.org/
NHNB: https://nhnb.org/fim/res/19935.html
Is it down: https://www.isitdownrightnow.com/4chan.org.html
reddit: https://www.reddit.com/r/technology/comments/1jzoofg/4chan_hacked_taken_down_emails_and_ips_leaked/
The Official thread by the man of the hour himself over on SoyJack.st: https://www.soyjak.st/soy/thread/10615723.html
The sharty's own summary of events: https://wiki.soyjak.st/The_Great_Cuckset
Janny logs: https://bvll.neocities.org/j/
/mlpol/ - My Little Politics
575 replies and 106 files omitted.
>>384443
As insufferable a faggot as XKCD is, he does have a good point on how to generate safe passwords.
As insufferable a faggot as XKCD is, he does have a good point on how to generate safe passwords.
>>384455
I send this to my users before I reset their password. Guess how many of them use the example provided?
I send this to my users before I reset their password. Guess how many of them use the example provided?
>>384458
0 because they're lazy bastards who probably changed only one character in their password.
>t. lazy faggot who does the same and relies on 2fa to cove his ass
0 because they're lazy bastards who probably changed only one character in their password.
>t. lazy faggot who does the same and relies on 2fa to cove his ass
>>384460
I bet you're one of those sites that have inane password requirements that make it impossible to generate
>password must be at least 8 characters...
>also this long password is invalid it must also be below 64 characters or whatever again for no reason
>you must include a letter, a number, and at least one of these special characters
>but those special characters are invalid for some reason
>yeah have fun setting the custom character set in your generator just for my website!
I bet you're one of those sites that have inane password requirements that make it impossible to generate
>password must be at least 8 characters...
>also this long password is invalid it must also be below 64 characters or whatever again for no reason
>you must include a letter, a number, and at least one of these special characters
>but those special characters are invalid for some reason
>yeah have fun setting the custom character set in your generator just for my website!
>>384465
>inane password requirements
Not particularly. Minimum of 8 alphanumeric characters, maximum of 64, 90 day lifespan, MFA is required. Fairly basic stuff, if a user can't create a password longer than 8 characters they'll be given a password. Service accounts have a minimum bit entropy of 128 with additional security measures.
>inane password requirements
Not particularly. Minimum of 8 alphanumeric characters, maximum of 64, 90 day lifespan, MFA is required. Fairly basic stuff, if a user can't create a password longer than 8 characters they'll be given a password. Service accounts have a minimum bit entropy of 128 with additional security measures.
>>384470
He does have a point. Most of those have no relation to how strong a password is. They just make them harder for you to remember.
He does have a point. Most of those have no relation to how strong a password is. They just make them harder for you to remember.
>>384449
>No one can hack/datamine a spiral-bound notebook
But like anon said, a keylogger can compromise the password as you use it. That's why I think it is critical to have a separate computer dedicated for any kind of online banking that you may partake in. That way you can minimize potential exposure to software vulnerabilities and malware.
>No one can hack/datamine a spiral-bound notebook
But like anon said, a keylogger can compromise the password as you use it. That's why I think it is critical to have a separate computer dedicated for any kind of online banking that you may partake in. That way you can minimize potential exposure to software vulnerabilities and malware.
>>384472
Hence >>384455
I try to encourage my users to actively understand the technology they are using. Unsurprisingly Accounts and HR are always lacking, which is annoyingly considering they are the most desirable targets.
>>384473
>keylogger can compromise the password as you use it.
I'm surprised people aren't more concerned with microsofts telemetry habits, or the incoming Recall feature.
Hence >>384455
I try to encourage my users to actively understand the technology they are using. Unsurprisingly Accounts and HR are always lacking, which is annoyingly considering they are the most desirable targets.
>>384473
>keylogger can compromise the password as you use it.
I'm surprised people aren't more concerned with microsofts telemetry habits, or the incoming Recall feature.
>>384474
Yes that's what I mean. Numbers and special characters don't faze a computer. They're only a problem for meatbags.
Yes that's what I mean. Numbers and special characters don't faze a computer. They're only a problem for meatbags.
>>384474
>I'm surprised people aren't more concerned with microsofts telemetry habits, or the incoming Recall feature.
People won't care until it, inevitably, blows up on microsoft in some huge way. Right now my banking PC uses windows out of convenience, but I'm probably going to transition to linux in the nearish future for it. My recreational PC is probably going to be stuck using windows 11 due to a mix of software compatibility for windows and my opinion that persisting on OS that is beyond EOL is a greater problem than dealing with 11's warts.
>>384475
>Yes that's what I mean. Numbers and special characters don't faze a computer
Here's the thing. It's not what computers are capable of doing, it's what the hackers instruct the computers to attempt. Including numbers and special characters within the character set used to brute force passwords does increase the amount of effort that a computer needs to check the possible combinations by an appreciable margin. They're usually not trying to hack you in particular. They just want to steal as many accounts as possible as quickly as possible because they're racing two clocks. The first clock is that the user might change their password in response to hearing about the data breach. The second clock is that a third party hacker who also bought a copy of the data from the data breach might hack the passwords first and steal the accounts before he can. A computer might not care about running through all of the permutations of numbers and special characters to brute force a password, but the hacker behind that computer sure fucking does because the expanded character set will slow down his brute forcing relative to the hackers who don't include the special characters. Consequently his more comprehensive cracking attempt is likely to lose the race to compromise the legions of shitty weak passwords.
tl;dr, this is sort of like that saying about encountering a grizzly bear while hiking in a group in the woods. You don't need to outrun the grizzly bear, you just need to outrun the slower people in the group. It's not about making your passwords uncrackable, it's about not being the low hanging fruit. The hackers are all chasing the low hanging fruit because weak passwords are everywhere and it is more profitable to pursue them.
>I'm surprised people aren't more concerned with microsofts telemetry habits, or the incoming Recall feature.
People won't care until it, inevitably, blows up on microsoft in some huge way. Right now my banking PC uses windows out of convenience, but I'm probably going to transition to linux in the nearish future for it. My recreational PC is probably going to be stuck using windows 11 due to a mix of software compatibility for windows and my opinion that persisting on OS that is beyond EOL is a greater problem than dealing with 11's warts.
>>384475
>Yes that's what I mean. Numbers and special characters don't faze a computer
Here's the thing. It's not what computers are capable of doing, it's what the hackers instruct the computers to attempt. Including numbers and special characters within the character set used to brute force passwords does increase the amount of effort that a computer needs to check the possible combinations by an appreciable margin. They're usually not trying to hack you in particular. They just want to steal as many accounts as possible as quickly as possible because they're racing two clocks. The first clock is that the user might change their password in response to hearing about the data breach. The second clock is that a third party hacker who also bought a copy of the data from the data breach might hack the passwords first and steal the accounts before he can. A computer might not care about running through all of the permutations of numbers and special characters to brute force a password, but the hacker behind that computer sure fucking does because the expanded character set will slow down his brute forcing relative to the hackers who don't include the special characters. Consequently his more comprehensive cracking attempt is likely to lose the race to compromise the legions of shitty weak passwords.
tl;dr, this is sort of like that saying about encountering a grizzly bear while hiking in a group in the woods. You don't need to outrun the grizzly bear, you just need to outrun the slower people in the group. It's not about making your passwords uncrackable, it's about not being the low hanging fruit. The hackers are all chasing the low hanging fruit because weak passwords are everywhere and it is more profitable to pursue them.
>>384470
>maximum of 64
Why? Even bcrypt takes up to 72. Argon2 and others can take much longer passwords. This is important to allow long passphrases.
>90 day lifespan
Also why? The only way for a user to comply with this is using a password manager, but if they use one they can generate a good enough password that brute forcing it would take 90 millenia, rather than 90 days. The rotation then just forces extra annoyance in having to go through the change procedure. And for anyone not using a manager it just leads to busywork e.g. having an incrementing number at the end of the password they increase every time, giving basically no extra security.
>>384474
>Unsurprisingly Accounts and HR are always lacking
Imho mandating a company-wide cloud password manager is probably a decent compromise. Yes >cloud but it's for a company. For example 1password I've seen used in some pretty security-conscious places. Then you just mandate that 1password is used for logins, and must also be used for password generation, and assuming HR karens are able to follow the most basic of instructions they shouldn't have any more issues with bad passwords.
>>384473
MFA is pretty good against keyloggers honestly. I'm not too worried about any of my accounts I have MFA on.
Hardware (U2F) where possible, but even TOTP makes it vastly harder to hijack even with full keylogger access. (Honestly it'd be easier to bundle the keylogger with a cookie stealer and hijack your session in most cases.)
>maximum of 64
Why? Even bcrypt takes up to 72. Argon2 and others can take much longer passwords. This is important to allow long passphrases.
>90 day lifespan
Also why? The only way for a user to comply with this is using a password manager, but if they use one they can generate a good enough password that brute forcing it would take 90 millenia, rather than 90 days. The rotation then just forces extra annoyance in having to go through the change procedure. And for anyone not using a manager it just leads to busywork e.g. having an incrementing number at the end of the password they increase every time, giving basically no extra security.
>>384474
>Unsurprisingly Accounts and HR are always lacking
Imho mandating a company-wide cloud password manager is probably a decent compromise. Yes >cloud but it's for a company. For example 1password I've seen used in some pretty security-conscious places. Then you just mandate that 1password is used for logins, and must also be used for password generation, and assuming HR karens are able to follow the most basic of instructions they shouldn't have any more issues with bad passwords.
>>384473
MFA is pretty good against keyloggers honestly. I'm not too worried about any of my accounts I have MFA on.
Hardware (U2F) where possible, but even TOTP makes it vastly harder to hijack even with full keylogger access. (Honestly it'd be easier to bundle the keylogger with a cookie stealer and hijack your session in most cases.)
>>384084
>DOB 2000-09-04
Jesus Christ. Pardon me for oldfagging, but there's something ridiculous about knowing you've been banned by people who were in diapers while you were on 4chan. No wonder the moderation on most boards sucks.
>DOB 2000-09-04
Jesus Christ. Pardon me for oldfagging, but there's something ridiculous about knowing you've been banned by people who were in diapers while you were on 4chan. No wonder the moderation on most boards sucks.
>>384482
If you have a dedicated machine that doesn't connect to the internet in ANY capacity, it's secure to an extent. Stuxnet was a thing after all.
>>384485
That's the limit of domain accounts I've set. I can't expect Josie in Accounts to remember a long sentence, given she can barely hold a casual conversation with her colleagues.
>90 day lifespan
Personally I'd have them change their passwords on the first of every month, but that was deemed as too 'problematic'.
>Adding a number to the end
Not a configured option. No new password can be related to any previously used ones.
>cloud password manager is probably a decent compromise
And I immediately stomped my foot down at that suggestion because it's fucking retarded.
>>384490
That's pretty cheap
If you have a dedicated machine that doesn't connect to the internet in ANY capacity, it's secure to an extent. Stuxnet was a thing after all.
>>384485
That's the limit of domain accounts I've set. I can't expect Josie in Accounts to remember a long sentence, given she can barely hold a casual conversation with her colleagues.
>90 day lifespan
Personally I'd have them change their passwords on the first of every month, but that was deemed as too 'problematic'.
>Adding a number to the end
Not a configured option. No new password can be related to any previously used ones.
>cloud password manager is probably a decent compromise
And I immediately stomped my foot down at that suggestion because it's fucking retarded.
>>384490
That's pretty cheap
>>384485
>MFA is pretty good against keyloggers honestly. I'm not too worried about any of my accounts I have MFA on.
Oh definitely. I didn't cover multi-factor authentication. I hope I didn't come off as inferring that it shouldn't be used. MFA should be used wherever possible. I just think that a standalone banking computer is a prudent extra step to help segregate work and play. I don't think that recreational computers can be assumed to be fully secure. But when it comes to protecting your retirement nest egg, I think that a 2nd computer used exclusively for banking is a reasonable extra safeguard that is more likely to be secure than a recreational computer. Granted nation state level actors probably still have backdoors into everything at a hardware level, but Uncle Sam probably isn't intending to steal your money via password cracking when it is so much easier for him to do that via inflation.
>Also why? The only way for a user to comply with this is using a password manager, but if they use one they can generate a good enough password that brute forcing it would take 90 millenia, rather than 90 days. The rotation then just forces extra annoyance in having to go through the change procedure
The problem is assuming that it will take 90 millenia to crack the password. That may be true today, but that isn't necessarily true for tomorrow. Advancements in mathematics or computational capabilities might identify flaws in the encryption algorithm or vastly improve our ability to perform calculations faster. Password expiration places additional strain on the attacker. Now simply being able to crack the password isn't good enough. They are now on a strict deadline to crack the password before it expires. This makes things more complicated and more expensive for an attacker.
>MFA is pretty good against keyloggers honestly. I'm not too worried about any of my accounts I have MFA on.
Oh definitely. I didn't cover multi-factor authentication. I hope I didn't come off as inferring that it shouldn't be used. MFA should be used wherever possible. I just think that a standalone banking computer is a prudent extra step to help segregate work and play. I don't think that recreational computers can be assumed to be fully secure. But when it comes to protecting your retirement nest egg, I think that a 2nd computer used exclusively for banking is a reasonable extra safeguard that is more likely to be secure than a recreational computer. Granted nation state level actors probably still have backdoors into everything at a hardware level, but Uncle Sam probably isn't intending to steal your money via password cracking when it is so much easier for him to do that via inflation.
>Also why? The only way for a user to comply with this is using a password manager, but if they use one they can generate a good enough password that brute forcing it would take 90 millenia, rather than 90 days. The rotation then just forces extra annoyance in having to go through the change procedure
The problem is assuming that it will take 90 millenia to crack the password. That may be true today, but that isn't necessarily true for tomorrow. Advancements in mathematics or computational capabilities might identify flaws in the encryption algorithm or vastly improve our ability to perform calculations faster. Password expiration places additional strain on the attacker. Now simply being able to crack the password isn't good enough. They are now on a strict deadline to crack the password before it expires. This makes things more complicated and more expensive for an attacker.
>>384492
>If you have a dedicated machine that doesn't connect to the internet in ANY capacity, it's secure to an extent. Stuxnet was a thing after all.
There is a bit of a power gap between
>I want to protect myself from the Five Eyes
and
>I want to protect my savings account from chinks, jeets, and the infamous hacker 4chan
>If you have a dedicated machine that doesn't connect to the internet in ANY capacity, it's secure to an extent. Stuxnet was a thing after all.
There is a bit of a power gap between
>I want to protect myself from the Five Eyes
and
>I want to protect my savings account from chinks, jeets, and the infamous hacker 4chan
>>384493
An interesting paper (https://ieeexplore.ieee.org/document/10934298) and news articles (US: https://www.forbes.com/sites/timothypapandreou/2024/12/16/googles-code-cracking-quantum-leap-heres-what-it-mean-for-business/ UK: https://www.theregister.com/2025/04/15/uk_quantum_funding/)
>>384494
>Five Eyes
https://torrentfreak.com/google-cloudflare-cisco-will-poison-dns-to-stop-piracy-block-circumvention-240613/
An interesting paper (https://ieeexplore.ieee.org/document/10934298) and news articles (US: https://www.forbes.com/sites/timothypapandreou/2024/12/16/googles-code-cracking-quantum-leap-heres-what-it-mean-for-business/ UK: https://www.theregister.com/2025/04/15/uk_quantum_funding/)
>>384494
>Five Eyes
https://torrentfreak.com/google-cloudflare-cisco-will-poison-dns-to-stop-piracy-block-circumvention-240613/
>>384492
>Personally I'd have them change their passwords on the first of every month, but that was deemed as too 'problematic'.
That completely doesn't answer "why".
>Not a configured option. No new password can be related to any previously used ones.
Assuming you're doing it by storing hashes of related passwords, any metric of "related" you use will be limited in some way and users will find some workaround that does let them use a related one. You cannot possibly pre-empt every possible mutation scheme an annoyed user that's being forced to change his password every three months will come up with.
>And I immediately stomped my foot down at that suggestion because it's fucking retarded.
Elaborate.
>>384493
>The problem is assuming that it will take 90 millenia to crack the password
There are certain realistic limits on computation to where around 200 bits or so of entropy, it starts becoming likely that a universe-sized computer operating at maximum theoretical efficiency would not be able to crack it before heat death. Now this does hinge on the definition of maximum theoretical efficiency but, while I don't remember the exact assumption, it was something pretty ridiculous and I think it's safe to say that we're not getting anywhere close to breaking that limit on a universe-sized computer any time soon.
And another thing is that even if one day it does become possible, it's pretty certain that it won't be within the next 90 days. Unless suddenly google announces Quantum Password Cracker 9000 available for commercial purchase out of fucking nowhere, but if that happens, you can just force a password expiry for all users at that exact point. And up till then, passwords that took 90 millenia to crack last quarter will still take just as much by next quarter, and there's no need to reset.
Besides, quantum computers are not a panacea and it's completely unclear whether they'll ever be useful for more than just a pretty limited set of algorithms. Maybe they will, but theoretical quantum algorithms have been under research for decades (completely independently from the engineering progress, since the algorithms are again purely theoretical) and we still aren't anywhere near any sort of general quantum computing model. So if you really want to be anal, use a quantum resistant hash, which as far as I can tell currently most good hashes basically are. And again, if a new paper comes out called New Quantum Algorithm That Completely Breaks SHA Family Hashes or something, then you a) update your backend to use a different hash and b) force-reset everyone's passwords.
Or just fucking wait because nobody has a working useful quantum computer yet and might not have any for decades. None of this warrants resetting every 90 days.
>Personally I'd have them change their passwords on the first of every month, but that was deemed as too 'problematic'.
That completely doesn't answer "why".
>Not a configured option. No new password can be related to any previously used ones.
Assuming you're doing it by storing hashes of related passwords, any metric of "related" you use will be limited in some way and users will find some workaround that does let them use a related one. You cannot possibly pre-empt every possible mutation scheme an annoyed user that's being forced to change his password every three months will come up with.
>And I immediately stomped my foot down at that suggestion because it's fucking retarded.
Elaborate.
>>384493
>The problem is assuming that it will take 90 millenia to crack the password
There are certain realistic limits on computation to where around 200 bits or so of entropy, it starts becoming likely that a universe-sized computer operating at maximum theoretical efficiency would not be able to crack it before heat death. Now this does hinge on the definition of maximum theoretical efficiency but, while I don't remember the exact assumption, it was something pretty ridiculous and I think it's safe to say that we're not getting anywhere close to breaking that limit on a universe-sized computer any time soon.
And another thing is that even if one day it does become possible, it's pretty certain that it won't be within the next 90 days. Unless suddenly google announces Quantum Password Cracker 9000 available for commercial purchase out of fucking nowhere, but if that happens, you can just force a password expiry for all users at that exact point. And up till then, passwords that took 90 millenia to crack last quarter will still take just as much by next quarter, and there's no need to reset.
Besides, quantum computers are not a panacea and it's completely unclear whether they'll ever be useful for more than just a pretty limited set of algorithms. Maybe they will, but theoretical quantum algorithms have been under research for decades (completely independently from the engineering progress, since the algorithms are again purely theoretical) and we still aren't anywhere near any sort of general quantum computing model. So if you really want to be anal, use a quantum resistant hash, which as far as I can tell currently most good hashes basically are. And again, if a new paper comes out called New Quantum Algorithm That Completely Breaks SHA Family Hashes or something, then you a) update your backend to use a different hash and b) force-reset everyone's passwords.
Or just fucking wait because nobody has a working useful quantum computer yet and might not have any for decades. None of this warrants resetting every 90 days.
>>384502
I always wondered: how do you use Rizon? All I saw was #4chan.
Do you need a password? An IP? I never understood how people used that as a chatroom. I tried, but I never get it.
I always wondered: how do you use Rizon? All I saw was #4chan.
Do you need a password? An IP? I never understood how people used that as a chatroom. I tried, but I never get it.
Watch out for a site being shilled that's called miladychan. It's run by an indian pedophile named Rohit Krishna Okhandiar who currently namefags as @charlottefang77 on twitter. He is a child groomer who previously ran a discord server that targeted underaged girls for self-harm.
I fucking knew it. They made it intentionally frustrating and unreliable to pressure you to buy gold accounts.
>>384515
Rizon is an IRC server, one of the few old big ones.
There is a pony IRC server too, irc.canternet.net if I recall.
hexchat is generally the preferred desktop IRC client, but there are probably thousands of others for every platform imaginable.
Rizon is an IRC server, one of the few old big ones.
There is a pony IRC server too, irc.canternet.net if I recall.
hexchat is generally the preferred desktop IRC client, but there are probably thousands of others for every platform imaginable.
>>384541
I lied, its irc.canternet.org, best if you use SSL.
canternet is in the list of servers by default, just scroll down, its in alphabetical order, and uses SSL by default.
I lied, its irc.canternet.org, best if you use SSL.
canternet is in the list of servers by default, just scroll down, its in alphabetical order, and uses SSL by default.
>>384540
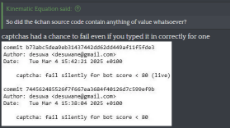
>captchas had a chance to fail even if you typed it in correctly
This has it backwards. When you type the captcha wrong, there's logic that will falsely show "post successful" if cloudflare thinks you're a bot (score < 80) AND you aren't a "known user". Not 100% sure what "known user" means, but it looks to be something like: you first posted >= 1 day ago and you've made >= 3 total posts. Once you've hit those thresholds, or if cloudflare thinks you're not a bot, none of this applies.
>captchas had a chance to fail even if you typed it in correctly
This has it backwards. When you type the captcha wrong, there's logic that will falsely show "post successful" if cloudflare thinks you're a bot (score < 80) AND you aren't a "known user". Not 100% sure what "known user" means, but it looks to be something like: you first posted >= 1 day ago and you've made >= 3 total posts. Once you've hit those thresholds, or if cloudflare thinks you're not a bot, none of this applies.
>>384502
I remember when the internet became popular in 1995. All the children from my highschool class (ALL if them) were able to use IRC (after being taught how to of course). Apart from a few people like me, none of them were nerds. Just regular people in secondary education (not even top level either). What happened to society that they have become unable to operate a simple program?
I remember when the internet became popular in 1995. All the children from my highschool class (ALL if them) were able to use IRC (after being taught how to of course). Apart from a few people like me, none of them were nerds. Just regular people in secondary education (not even top level either). What happened to society that they have become unable to operate a simple program?
>>384549
Public education is uninterested in teaching children how to think critically for themselves, communicate effectively, or organize beyond the next meal.
Parents are kept too busy to teach children anything beyond how to wipe their own bum.
Public education is uninterested in teaching children how to think critically for themselves, communicate effectively, or organize beyond the next meal.
Parents are kept too busy to teach children anything beyond how to wipe their own bum.
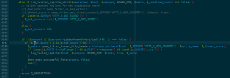
>>384564
It's a bit more complicated than that - there are a bunch of different checks in the isUserKnown function. The cookie needs to be at least 1 day old and have 3 posts associated with it, and there are other checks about how recently / how often you've changed IP addresses while keeping the same cookie
It's a bit more complicated than that - there are a bunch of different checks in the isUserKnown function. The cookie needs to be at least 1 day old and have 3 posts associated with it, and there are other checks about how recently / how often you've changed IP addresses while keeping the same cookie
>>384546
Where's the complete source code leak including the captcha? I only have the source code for the main site.
Where's the complete source code leak including the captcha? I only have the source code for the main site.
Holy shit I can't believe this place still exists but I'm glad it does, came here via Kiwi Farms.
You guys have probably discussed it ad nauseam but they were running a 15 year old unsupported OS and hadn't updated the code since Moot left, I am shocked this didn't happen sooner and with the source code leak it is 100% gonna happen again when they come back online unless they completely rewrite it or just admit defeat and switch to Tinyboard or something.
I'm astonished by the level of incompetence and stupidity.
You guys have probably discussed it ad nauseam but they were running a 15 year old unsupported OS and hadn't updated the code since Moot left, I am shocked this didn't happen sooner and with the source code leak it is 100% gonna happen again when they come back online unless they completely rewrite it or just admit defeat and switch to Tinyboard or something.
I'm astonished by the level of incompetence and stupidity.
>>384579
>I'm astonished by the level of incompetence and stupidity.
Astonished certainly isn't the word I would use...
>I'm astonished by the level of incompetence and stupidity.
Astonished certainly isn't the word I would use...
>>384580
...fair, the only thing they changed since Hiro took over was the captcha and we all saw what unusable shit that was.
...fair, the only thing they changed since Hiro took over was the captcha and we all saw what unusable shit that was.
Also the janny exodus is supposedly real
https://kiwifarms.net/threads/4chan.37222/post-21146301
I wouldn't stick around either if I was getting doxed for $0
https://kiwifarms.net/threads/4chan.37222/post-21146301
I wouldn't stick around either if I was getting doxed for $0
>>384591
funniest thing in that is fact that moderation has been already shown to be full of shit, meaning rules were followed and not followed wantonly and boards turned shit due it. So that reads pretty much "oh nooo, we didn't do shit before this and if people leave, then we would need to do shit and we don't want to do shit, we want things to be as they were". So yeah, no hope there.
funniest thing in that is fact that moderation has been already shown to be full of shit, meaning rules were followed and not followed wantonly and boards turned shit due it. So that reads pretty much "oh nooo, we didn't do shit before this and if people leave, then we would need to do shit and we don't want to do shit, we want things to be as they were". So yeah, no hope there.
>>384591
I felt like this would happen. Paid shills and jannies won't get paid to do nothing. They will find new jobs.
It's USAID for 4chan spammers. It's going to lead right back to the glowniggers handling these shills.
>>384620
It's for the best. People will regroup. If it does come back it's going to be the new reddit.
I felt like this would happen. Paid shills and jannies won't get paid to do nothing. They will find new jobs.
It's USAID for 4chan spammers. It's going to lead right back to the glowniggers handling these shills.
>>384620
It's for the best. People will regroup. If it does come back it's going to be the new reddit.
Hey anons, I came back to congratulate you all
In the end, /mlpol/ outlived /pol/, it outlived all of 4chan. Congrats guys! mlpol.net is the best bunker after all!
In the end, /mlpol/ outlived /pol/, it outlived all of 4chan. Congrats guys! mlpol.net is the best bunker after all!
>>384631
>/mlpol/ outlasted /pol/
That's like saying you lost your limbs but are still alive. Thank you anon for the sentiment, but you'll hear no cheers from his end of the gallery
>/mlpol/ outlasted /pol/
That's like saying you lost your limbs but are still alive. Thank you anon for the sentiment, but you'll hear no cheers from his end of the gallery
>>384579
>You guys have probably discussed it ad nauseam but they were running a 15 year old unsupported OS
Yeah, it's outrageous. WTF were their admins fucking doing? Just fucking each other in the ass all day? It's bad to be slow on your software updates. It's worse to be slow enough that your software reaches EOL. You can't make it up that you let it stay EOL for a decade and a half.
>You guys have probably discussed it ad nauseam but they were running a 15 year old unsupported OS
Yeah, it's outrageous. WTF were their admins fucking doing? Just fucking each other in the ass all day? It's bad to be slow on your software updates. It's worse to be slow enough that your software reaches EOL. You can't make it up that you let it stay EOL for a decade and a half.
[Reply] [Last 50 Posts] [Last 100 Posts] [Last 200 Posts]
You are viewing older replies. Click [View All] or [Last n Posts] to vew latest posts.
Clicking update will load all posts posted after last post on this page.
Post pagination: [Prev] [1-50] [51-100] [101-150] [151-200] [201-250] [251-300] [301-350] [351-400] [401-450] [451-500] [501-550] [551-600] [601-625] [Next] [Live (last 50 replies)]
625 replies | 118 files | 189 UUIDs | Page 4