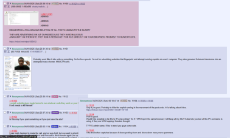
Based on the replies to the original post on there the info in the picture seems legit.
"Not a web-dev guy, but does this essentially mean they have the ability for remote code execution on your machine, via a direct socket and not through the browser?"
reply to this question:
"Yes, they have an RCE to your browser's sandbox. But surpisingly one can scan all localhost ports through this sandbox, for example..."
So be careful using that site. Best course of action is turning off pretty much everything and just lurk for new info.
/mlpol/ - My Little Politics
121 replies and 28 files omitted.
>>385492
I've never been to that chan, and didn't really know it existed until the hack, so am I safe?
I've never been to that chan, and didn't really know it existed until the hack, so am I safe?
>>385492
UH OH.
Sharty are CIA backed glownigger trannies. They are heavily connected to the O9a/the com grooming/abuse/blackmail cult.
Isn't if funny they claim to be "soyteens" aka a bunch of 10 year olds posting soyjaks, but they have malicious javascript on their site?
UH OH.
Sharty are CIA backed glownigger trannies. They are heavily connected to the O9a/the com grooming/abuse/blackmail cult.
Isn't if funny they claim to be "soyteens" aka a bunch of 10 year olds posting soyjaks, but they have malicious javascript on their site?
>>385492
Also the sharty are the literal grooming trannies who spam blacked and trannies. Now they are spamming 8/trash/ with blacked since 4chan is down.
Also the sharty are the literal grooming trannies who spam blacked and trannies. Now they are spamming 8/trash/ with blacked since 4chan is down.
>>385492
They called it the 'discord scanner' when I last looked. Entire site seemed sketchy as hell.
They called it the 'discord scanner' when I last looked. Entire site seemed sketchy as hell.
>>385526
if they all turn to trannies, then it only be a matter of time before they all kill themselves, seems like a self correcting issue.
if they all turn to trannies, then it only be a matter of time before they all kill themselves, seems like a self correcting issue.
According to some users, it's the "anti 'cord" feature which checks to see if you have discord open, otherwise it doesn't let you post.
>>385492
>"Not a web-dev guy, but does this essentially mean they have the ability for remote code execution on your machine, via a direct socket and not through the browser?"
>reply to this question:
>"Yes, they have an RCE to your browser's sandbox. But surpisingly one can scan all localhost ports through this sandbox, for example..."
Dumb retards.
I cannot stress this enough, visiting any website using a browser that has javascript enabled gives that website RCE into your browser's sandbox. The first quote is clearly asking if this gives access "on your machine, via a direct socket and not through the browser", and the answer "yes, in the browser" is nonsensical because it is literally "no". I don't know why that anon said "yes".
One can scan all ports through javascript, yes. You don't need this wasm websocket thingy to do that. Again, any website can do that at any time, unless you've turned off JS in your browser.
Now with that being said, the only purpose of this kind of mechanism is going to be obfuscation: i.e. making it harder to see what javascript it runs. The normal way to include scripts is as a file that's really easy to see in the browser console, so doing it this way makes you require to log all the websocket requests and reassemble the file yourself thus making it much harder to actually read it.
So in itself this is not malicious, but obfuscating the code this hard is definitely indicative of malicious stuff.
>>385531
>>385544
I don't know, maybe discord electron uses some non-HTTP ports for its networking?
Also, it doesn't prevent you from posting, from what I've heard it just gives your posts a "discordfag" tag visible to jannies.
>>385541
I haven't looked into the site myself but just based on the OP it sounds like it probably executes by default, so no, you're not safe. Sounds like if you specifically block the script, then you won't be able to post, but without further info there's no reason to assume it wouldn't run automatically if you haven't blocked it.
[Read more] >"Not a web-dev guy, but does this essentially mean they have the ability for remote code execution on your machine, via a direct socket and not through the browser?"
>reply to this question:
>"Yes, they have an RCE to your browser's sandbox. But surpisingly one can scan all localhost ports through this sandbox, for example..."
Dumb retards.
I cannot stress this enough, visiting any website using a browser that has javascript enabled gives that website RCE into your browser's sandbox. The first quote is clearly asking if this gives access "on your machine, via a direct socket and not through the browser", and the answer "yes, in the browser" is nonsensical because it is literally "no". I don't know why that anon said "yes".
One can scan all ports through javascript, yes. You don't need this wasm websocket thingy to do that. Again, any website can do that at any time, unless you've turned off JS in your browser.
Now with that being said, the only purpose of this kind of mechanism is going to be obfuscation: i.e. making it harder to see what javascript it runs. The normal way to include scripts is as a file that's really easy to see in the browser console, so doing it this way makes you require to log all the websocket requests and reassemble the file yourself thus making it much harder to actually read it.
So in itself this is not malicious, but obfuscating the code this hard is definitely indicative of malicious stuff.
>>385531
>>385544
I don't know, maybe discord electron uses some non-HTTP ports for its networking?
Also, it doesn't prevent you from posting, from what I've heard it just gives your posts a "discordfag" tag visible to jannies.
>>385541
I haven't looked into the site myself but just based on the OP it sounds like it probably executes by default, so no, you're not safe. Sounds like if you specifically block the script, then you won't be able to post, but without further info there's no reason to assume it wouldn't run automatically if you haven't blocked it.
>>385620
Doc, when shit went down I browsed their site for a couple hours gathering information. How long do I have to live?
Kidding aside, if there's anything to mitigate any exposure, I and others who won't admit it would appreciate that information
Doc, when shit went down I browsed their site for a couple hours gathering information. How long do I have to live?
Kidding aside, if there's anything to mitigate any exposure, I and others who won't admit it would appreciate that information
I wouldn't dismiss the possibility. Something about that unique sharty user brainrot can lead some dudes with a little code knowhow to just decide to do virtual ultraviolence.
4chan deserves every ounce of it, so I don't feel too devestated even though it's my preferred place of chicanery.
4chan deserves every ounce of it, so I don't feel too devestated even though it's my preferred place of chicanery.
Didn't the sharty have ties to foreign intelligence as well?
>>385628
Realistically speaking assuming your browser is up to date, the worst they can do is fingerprint you.
Note that port scanning using javascript is based on timeouts, javascript can't actually send anything to those ports so it's just a binary "open/closed" datapoint, not a vector for any further attacks. Really, if they wanted to do malicious shit, they'd just use your IP that you connect with and port-knock serverside, with the ability to try to exploit any open ports they see, but that would also be literally illegal to the point where they would get shutdown unless the servers are hosted in some secret third world country with no enforcement or something. Also, the average desktop computer shouldn't have any vulnerable ports open by default - the issue arises if you run any sort of server-like software that listens to a port and that software happens to be vulnerable, but if you're not running anything like that you're pretty safe - again assuming your OS is up to date.
In theory 0-days exist but it seems astoundingly unlikely that the sharty is using a 0-day of all things on its users.
And if nothing else, you can also take comfort that the sharty gets thousands of users, especially now that it's literally getting a flood of 4chan refugees, so it's extremely unlikely they will care about you specifically or do anything with any of the fingerprinting info they gathered.
[Read more] Realistically speaking assuming your browser is up to date, the worst they can do is fingerprint you.
Note that port scanning using javascript is based on timeouts, javascript can't actually send anything to those ports so it's just a binary "open/closed" datapoint, not a vector for any further attacks. Really, if they wanted to do malicious shit, they'd just use your IP that you connect with and port-knock serverside, with the ability to try to exploit any open ports they see, but that would also be literally illegal to the point where they would get shutdown unless the servers are hosted in some secret third world country with no enforcement or something. Also, the average desktop computer shouldn't have any vulnerable ports open by default - the issue arises if you run any sort of server-like software that listens to a port and that software happens to be vulnerable, but if you're not running anything like that you're pretty safe - again assuming your OS is up to date.
In theory 0-days exist but it seems astoundingly unlikely that the sharty is using a 0-day of all things on its users.
And if nothing else, you can also take comfort that the sharty gets thousands of users, especially now that it's literally getting a flood of 4chan refugees, so it's extremely unlikely they will care about you specifically or do anything with any of the fingerprinting info they gathered.
>>385725
>worst is fingerprinting
you forgot cryptomining, specially now that webgpu is a thing.
for example: https://github.com/TalDerei/Web-Mining
>worst is fingerprinting
you forgot cryptomining, specially now that webgpu is a thing.
for example: https://github.com/TalDerei/Web-Mining
>>385524
It's almost like them hacking 4chan is them wanting to put an end to twitter/redditors getting red pilled from visiting /pol/, and further spreading the anti-semitism diease on their normiespheres. They're not going to bother coming to these alt-chan sites, so it's a total kike victory if 4chan remains down, or if anons don't remigrate when it does come back up.
It's almost like them hacking 4chan is them wanting to put an end to twitter/redditors getting red pilled from visiting /pol/, and further spreading the anti-semitism diease on their normiespheres. They're not going to bother coming to these alt-chan sites, so it's a total kike victory if 4chan remains down, or if anons don't remigrate when it does come back up.
>>385763
I'm not completely certain but I'm 99% sure that it's impossible to do in the background without user authorization. So if you close the site, the cryptominer stops.
It's a shady thing to do but it doesn't really harm you, and doesn't affect you in any way as soon as you leave the site.
I'm not completely certain but I'm 99% sure that it's impossible to do in the background without user authorization. So if you close the site, the cryptominer stops.
It's a shady thing to do but it doesn't really harm you, and doesn't affect you in any way as soon as you leave the site.
>>385841
See, this gets into the problem of Soyjack as an entity/site (or what I would describe as a problem in the greater context of "You shut down 4chan"). It's like Jeff Goldblum said in Jurrassic Park; you got so caught up in whether or not you could that you forgot to ask whether you should. Oh yes, sure, you knocked down the king, but where does that put you?
>Oh, we weren't trying to take 4chan's place!
We? It seems like one anon is competent, and the rest of you are apron-hangers.
See, this gets into the problem of Soyjack as an entity/site (or what I would describe as a problem in the greater context of "You shut down 4chan"). It's like Jeff Goldblum said in Jurrassic Park; you got so caught up in whether or not you could that you forgot to ask whether you should. Oh yes, sure, you knocked down the king, but where does that put you?
>Oh, we weren't trying to take 4chan's place!
We? It seems like one anon is competent, and the rest of you are apron-hangers.
>>385845
I'm honestly not sure what you're talking about. Is the sharty supposed to step up as a 4chan replacement? I don't think it can end up as one just because of how specific the culture is there, it's a shitposting place through and through and you can't just use it as a replacement for all the boards 4chan had. They could of course go in that direction if they wanted to but it's really up to them to decide.
Right now they're obviously drowning in traffic but that's not due to being "second place", that's just due to them instantly gaining tremendous infamy and being in the news.
As for "whether or not you should", I don't think they put anywhere nearly that much thought into it. Again, it's purely a shitposting place, a malicious one at that these days. Didn't really use to be back on /qa/ but now it is. And 4chan killed /qa/ so now the heir to /qa/ killed 4chan, simple as.
What's it to them anyway? They're an altchan splinter steeped in the worst of shitposting culture. The worst that will happen is that the traffic surge causes it to shut down, five replacement splinters pop up, they have a mutual raiding war, three of the splinters' admins get outed as being IRL pedos, and two weeks later the official site goes back up under a new domain or something. They won't care, and there's not much that can threaten them when they're already on the lowest rung of existence like this.
They shut down 4chan, they won ("/qa/ won"), and that's what matters to them and that's what will be remembered in the end.
[Read more] I'm honestly not sure what you're talking about. Is the sharty supposed to step up as a 4chan replacement? I don't think it can end up as one just because of how specific the culture is there, it's a shitposting place through and through and you can't just use it as a replacement for all the boards 4chan had. They could of course go in that direction if they wanted to but it's really up to them to decide.
Right now they're obviously drowning in traffic but that's not due to being "second place", that's just due to them instantly gaining tremendous infamy and being in the news.
As for "whether or not you should", I don't think they put anywhere nearly that much thought into it. Again, it's purely a shitposting place, a malicious one at that these days. Didn't really use to be back on /qa/ but now it is. And 4chan killed /qa/ so now the heir to /qa/ killed 4chan, simple as.
What's it to them anyway? They're an altchan splinter steeped in the worst of shitposting culture. The worst that will happen is that the traffic surge causes it to shut down, five replacement splinters pop up, they have a mutual raiding war, three of the splinters' admins get outed as being IRL pedos, and two weeks later the official site goes back up under a new domain or something. They won't care, and there's not much that can threaten them when they're already on the lowest rung of existence like this.
They shut down 4chan, they won ("/qa/ won"), and that's what matters to them and that's what will be remembered in the end.
>>385841
Point there isn't get jackpot situations (someone with 5090 leaving tab open while sleeping), but bit of calculation from here and there, with few constant sources where someone forgets tab open and it gets to work longer time. Also how miners usually operate is that they have idle detection algorithms, although those have random success in browser. But point being that script tries to run when it detects that machine is idling, also more sophisticated ones wont do calculations full blast so they don't cause fans to go full blast.
Point there isn't get jackpot situations (someone with 5090 leaving tab open while sleeping), but bit of calculation from here and there, with few constant sources where someone forgets tab open and it gets to work longer time. Also how miners usually operate is that they have idle detection algorithms, although those have random success in browser. But point being that script tries to run when it detects that machine is idling, also more sophisticated ones wont do calculations full blast so they don't cause fans to go full blast.
>>385857
Oh, right. Yeah. I'm definitely not saying having a miner isn't shady, or that it can't be profitable.
I'm saying that as a user, it's very easy to protect yourself: just close the tab lmao. It's also not a big concern if you visit the site: they'll take some free electricity from you but it'll likely be less than pennies. Again, it's a shady thing to do, but it's not like they'll hack your browser or fingerprint you and sell your data or anything.
But of course that's not to say the sharty isn't fingerprinting you. I haven't analysed any code they're sending or anything. I'm just saying that, as a casual visitor, I'd be way more concerned with fingerprinting and data harvesting (giving them data that they will keep saved even after I leave the site) than with a cryptominer.
Unless said cryptominer just maxes out my GPU to 100% and slows down my entire PC of course but people would've noticed that by now if it did anything of the sort. And again, EVEN then, it's just a matter of "oh, what a shitty site, I'm gonna close that tab and not visit again" and not "oh darn I visited them once without a script blocker now they have a full profile of my browser and OS and running services".
[Read more] Oh, right. Yeah. I'm definitely not saying having a miner isn't shady, or that it can't be profitable.
I'm saying that as a user, it's very easy to protect yourself: just close the tab lmao. It's also not a big concern if you visit the site: they'll take some free electricity from you but it'll likely be less than pennies. Again, it's a shady thing to do, but it's not like they'll hack your browser or fingerprint you and sell your data or anything.
But of course that's not to say the sharty isn't fingerprinting you. I haven't analysed any code they're sending or anything. I'm just saying that, as a casual visitor, I'd be way more concerned with fingerprinting and data harvesting (giving them data that they will keep saved even after I leave the site) than with a cryptominer.
Unless said cryptominer just maxes out my GPU to 100% and slows down my entire PC of course but people would've noticed that by now if it did anything of the sort. And again, EVEN then, it's just a matter of "oh, what a shitty site, I'm gonna close that tab and not visit again" and not "oh darn I visited them once without a script blocker now they have a full profile of my browser and OS and running services".
>>385871
Nigger all malware is not created equal. My point is that malware that a) does nothing to your PC, b) does nothing to your personal data, and c) ceases to have any effect in the present and future as soon as you turn off the site - is among the least concerning types of malware.
Nigger all malware is not created equal. My point is that malware that a) does nothing to your PC, b) does nothing to your personal data, and c) ceases to have any effect in the present and future as soon as you turn off the site - is among the least concerning types of malware.
>>385873
That's a slippery slope. The 'least concerning type of malware' might eventually replace ads, because it's 'not harmful' anyway, and people want E-money.
That's a slippery slope. The 'least concerning type of malware' might eventually replace ads, because it's 'not harmful' anyway, and people want E-money.
>>385895
>the least concerning type of malware might eventually replace a much more concerning type of malware (pervasive tracking)
oh noooo
Anyway that's not even the point here, the entire conversation started from an anon asking "am I fucked from having visited the sharty?". The answer is probably not, but if hypothetically all they were doing was cryptomining and nothing else, the answer would've been most definitely not, if you've closed the tab you are no longer affected in any way shape or form.
>the least concerning type of malware might eventually replace a much more concerning type of malware (pervasive tracking)
oh noooo
Anyway that's not even the point here, the entire conversation started from an anon asking "am I fucked from having visited the sharty?". The answer is probably not, but if hypothetically all they were doing was cryptomining and nothing else, the answer would've been most definitely not, if you've closed the tab you are no longer affected in any way shape or form.
>>385899
>"am I fucked from having visited the sharty?"
>probably not
That's not very reassuring for a site that's only supposed to be a alt-chan type of site. They clearly have something else going on for them in the background that we don't know about, if they're willing to run such things on their website. You coming off as a shill seems to confirm that that site has connections to glowies.
>>385901
no you're not
>"am I fucked from having visited the sharty?"
>probably not
That's not very reassuring for a site that's only supposed to be a alt-chan type of site. They clearly have something else going on for them in the background that we don't know about, if they're willing to run such things on their website. You coming off as a shill seems to confirm that that site has connections to glowies.
>>385901
no you're not
>>385901
Thats fine, we're receptive to refugees! But, we're also on guard for douchebags, cuz IDK if you heard but theres alot of homeless douchebags right about now
Thats fine, we're receptive to refugees! But, we're also on guard for douchebags, cuz IDK if you heard but theres alot of homeless douchebags right about now
>>385903
>That's not very reassuring for a site that's only supposed to be a alt-chan type of site.
Yeah no shit.
>You coming off as a shill
Nigger all I was doing is trying to take a realistic look at what the threat is.
The entire conversation about cryptominers is moot anyway regarding the sharty because again I DON'T KNOW WHAT THEY DO. And I think it's pretty likely they fingerprint you out the ass. So no, I do not think you should visit them.
But just yelling "sharty bad! sharty bad!" is irrelevant in a technical discussion. I entered a technical discussion thread. Just because I then started discussing the technical implications of things doesn't mean I'm a fucking shill, we can talk about "sharty bad" in threads that aren't explicitly about the technical aspects of their javascript code.
For example the OP's quotes can almost be read as "the sharty can literally hack your computer" which is objectively false (unless they literally get 0-days fed to them by the feds, because they sure as fuck aren't finding any 0-days in a major browser themselves lmao). And I'm not saying that to shill for it, I'm saying that because it is good to have a clear understanding of what a threat is. Panicking "I visited the sharty does this mean I am hacked now??" doesn't help anyone, if anything I bet they'd be absolutely chuffed to know they caused a bunch of retards to think they got hacked.
I also think cryptominers would be better for online privacy than ad networks. I also think you should not visit the sharty, at least not without a well configured script blocker. These are not somehow mutually exclusive.
>no you're not
Suck my balls
>>385905
Thanks, it has definitely been very comfy here so far
[Read more] >That's not very reassuring for a site that's only supposed to be a alt-chan type of site.
Yeah no shit.
>You coming off as a shill
Nigger all I was doing is trying to take a realistic look at what the threat is.
The entire conversation about cryptominers is moot anyway regarding the sharty because again I DON'T KNOW WHAT THEY DO. And I think it's pretty likely they fingerprint you out the ass. So no, I do not think you should visit them.
But just yelling "sharty bad! sharty bad!" is irrelevant in a technical discussion. I entered a technical discussion thread. Just because I then started discussing the technical implications of things doesn't mean I'm a fucking shill, we can talk about "sharty bad" in threads that aren't explicitly about the technical aspects of their javascript code.
For example the OP's quotes can almost be read as "the sharty can literally hack your computer" which is objectively false (unless they literally get 0-days fed to them by the feds, because they sure as fuck aren't finding any 0-days in a major browser themselves lmao). And I'm not saying that to shill for it, I'm saying that because it is good to have a clear understanding of what a threat is. Panicking "I visited the sharty does this mean I am hacked now??" doesn't help anyone, if anything I bet they'd be absolutely chuffed to know they caused a bunch of retards to think they got hacked.
I also think cryptominers would be better for online privacy than ad networks. I also think you should not visit the sharty, at least not without a well configured script blocker. These are not somehow mutually exclusive.
>no you're not
Suck my balls
>>385905
Thanks, it has definitely been very comfy here so far
>>385492
So since there's an ongoing shilling campaign that's been rolled out on altchans to get refugees onto the sharty, should the sharty be completely wordfiltered in light of the OP malicious code?
I'm leaning on yes, but does Lotus or Pupper know about this?
So since there's an ongoing shilling campaign that's been rolled out on altchans to get refugees onto the sharty, should the sharty be completely wordfiltered in light of the OP malicious code?
I'm leaning on yes, but does Lotus or Pupper know about this?
>>385833
So it's total kike victory if we don't go back to the containment zone?
I rather be here where we can be free range anons
So it's total kike victory if we don't go back to the containment zone?
I rather be here where we can be free range anons
I go to sleep wake up and 4chan is gone forever, the hell did I miss?
were it not for the rules of this board I would be fucking with you so hard

1745214661.mov (5.2 MB, Resolution:568x320 Length:00:00:54, dancingwiththedj.mov) [play once] [loop]

>>386090
so there I was browsing /pol/ one day like the voices told me to, and holy shit there was ponies everywhere and I knew I had to do something about this
so there I was browsing /pol/ one day like the voices told me to, and holy shit there was ponies everywhere and I knew I had to do something about this
1745215338_1.png (2.1 MB, 1024x1536, 76b7f4a7-e75b-4b29-a82c-849ea4dae5bc.png)

1745215436.mp4 (5.8 MB, Resolution:1280x720 Length:00:00:21, [Anthology 7 Short] Rainbow Stalin.mp4) [play once] [loop]
![[Anthology 7 Short] Rainbow Stalin.mp4](/images/thumb/7B889FB79A978F0E32E53969E9EDD35A-6097918.png)
>>385620
Interesting. I’ll take your word for it. I never went to the sharty. I mean, who knows who’s behind it? Seems sus.
Interesting. I’ll take your word for it. I never went to the sharty. I mean, who knows who’s behind it? Seems sus.
>>385620
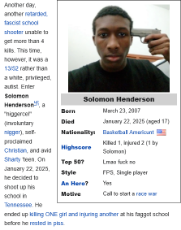
The biggest issue is they are a know malicious website. They are backed by glowniggers. They groomed Solomon Henderson into a mass shooter. donkey show trannies are shitting up every board with subtle ads for their site.
>>386105
>>386093
Tamers12345 is being 100% astroturfed by the donkey show BTW. That's where all his inorganic support and view bots come from.
The biggest issue is they are a know malicious website. They are backed by glowniggers. They groomed Solomon Henderson into a mass shooter. donkey show trannies are shitting up every board with subtle ads for their site.
>>386105
>>386093
Tamers12345 is being 100% astroturfed by the donkey show BTW. That's where all his inorganic support and view bots come from.
Test, donkey show. Based if it's a word filter. Or it's autocorrect.
I've come to notice that having a captcha system (with no pass) keeps shills away. This site could benefit from a captcha system
>>386314
Ah okay. I haven't seen their ad spam yet, but demoralizing shilling and jewish d&c style posting yes
Ah okay. I haven't seen their ad spam yet, but demoralizing shilling and jewish d&c style posting yes
>>386320
They post sutble advertisements like
>X's board is slower than this one
>I compared X to Y and X is slightly better
>Anyone tried X?
Etc
They post sutble advertisements like
>X's board is slower than this one
>I compared X to Y and X is slightly better
>Anyone tried X?
Etc
>>386352
>To be honest, I rather deal with the shills then dealing with captcha.
That's gonna be a controversial opinion.
Maybe if it was google recaptcha v3, then I could perhaps see myself agreeing. But a nice text-based captcha? Nah, I'd much rather less spam at the cost of spending like 5 seconds extra when making a post.
>To be honest, I rather deal with the shills then dealing with captcha.
That's gonna be a controversial opinion.
Maybe if it was google recaptcha v3, then I could perhaps see myself agreeing. But a nice text-based captcha? Nah, I'd much rather less spam at the cost of spending like 5 seconds extra when making a post.
>>386364
Without having checked recently, if the site captcha is anything like the Ponerpics captcha, you don't want it
Without having checked recently, if the site captcha is anything like the Ponerpics captcha, you don't want it
>>386365
Yeah, that one is based in principle but not very keyboard-able.
Unironically 4chan's captcha was not bad at all these days. The only good thing 4chan did in recent years, was actually replacing the fucking abomination for which I have no words that was recaptcha v3, with a custom made thingy that was actually surprisingly usable.
Yeah, that one is based in principle but not very keyboard-able.
Unironically 4chan's captcha was not bad at all these days. The only good thing 4chan did in recent years, was actually replacing the fucking abomination for which I have no words that was recaptcha v3, with a custom made thingy that was actually surprisingly usable.
>>386364
With captcha and a 10 minute wait, 4chan was still getting spam.
The way I see it, there's no point. We'll have to deal with them as we see them.
Despite the huge number of new users, the amount of shills and spam is not that bad. And if you look at the site's statistics, the amount of users is doing down which mean there should be less shills/spammers.
With captcha and a 10 minute wait, 4chan was still getting spam.
The way I see it, there's no point. We'll have to deal with them as we see them.
Despite the huge number of new users, the amount of shills and spam is not that bad. And if you look at the site's statistics, the amount of users is doing down which mean there should be less shills/spammers.
>>386399
Captcha didn't stop spammers and shills because they had passes. If this site had captcha and no pass, there wont be spammers or shills, because soon they'll be here too.
Captcha didn't stop spammers and shills because they had passes. If this site had captcha and no pass, there wont be spammers or shills, because soon they'll be here too.
>>386399
>We'll have to deal with them as we see them.
VPN, VPS, .gov, and Indians.
They all followed the same templates too.
>We'll have to deal with them as we see them.
VPN, VPS, .gov, and Indians.
They all followed the same templates too.
>I need to talk about HEEBS
>PAJEETS
>MOON CRICKETS
Help
>PAJEETS
>MOON CRICKETS
Help
>>386399
Thats because mlpol isn't the spam and shills main target. 8moe absorbed the majority of 4chan, and /mlp/ was an exception since it was already a dead board. Just like when 8 chan (original) got too much freedom they were attacked and brought down.
You can read their status dealing with it daily, be happy that mlpol is still a niche board that isn't worth the resources... yet
https://8chan.moe/site/res/5423.html#11150
Thats because mlpol isn't the spam and shills main target. 8moe absorbed the majority of 4chan, and /mlp/ was an exception since it was already a dead board. Just like when 8 chan (original) got too much freedom they were attacked and brought down.
You can read their status dealing with it daily, be happy that mlpol is still a niche board that isn't worth the resources... yet
https://8chan.moe/site/res/5423.html#11150
>>386440
Well, to that end no one has looked at mlpol and thought "I can profit off this", and that's by design. There never has been and arguably never will be marketability or profitability in this site, other than free speech, ponies, shitposting, etc.
Well, to that end no one has looked at mlpol and thought "I can profit off this", and that's by design. There never has been and arguably never will be marketability or profitability in this site, other than free speech, ponies, shitposting, etc.
1745313349.mp4 (8.5 MB, Resolution:1920x1080 Length:00:01:58, O9A quick summary.mp4) [play once] [loop]

>>385833
>it's a total kike victory if 4chan remains down
>hacking 4chan is them wanting to put an end to twitter/redditors getting red pilled from visiting /pol/, and further spreading the anti-semitism diease on their normiespheres
No one in the past 8 years has been getting red pilled from visiting /pol/ but they have been psyopped. The true reason why 4chan went down is because they lost their funding. They even made an april fool's joke out of it. Since 2016, 4chan survived off federal gibs (but through unofficial channels). Hence why gookmoot has been so silent ever since Trump was meme'd into office: the old US elites were pretty pissed. But he needed money to keep 4chan alive and he probably figured it was in his best interest to take a deal from US glowniggers.
In 2020 Trump lost because dems cheated. The amount of internet censorship at this time was insane. Even on 4pol you could get moderated talking about it, not consistently, but still. But to talk about the steal on normieplatforms? Impossible. And mind you, I'm not even American, I'm a Eurofag. My theory is that they first needed 4 more years of Biden to start to Ukraine war and lay the groundwork for that conflict. But after that, they would let Trump in again and crash the global economy. So far... based off of the chaos we're seeing, I think my theory holds.
But the point I'm trying to make is this: 4chan is owned by gookmoot who is not under the thumb of the pro Trump glowniggers. So that's why they simply terminated it. And they were pretty open about it: see picrel. The satanic glownigger faction knew that 4chan would be terminated at some point and that's why donkey show exists: it's the fallback base. So when they pulled the plug at 4chan, they made a nice little story about a hack. The media shilled the soyjak URL and the 4chan userbase migrated there. Go on donkey showpol right now and if you cannot unsee the similarity with 4pol.
I guarantee you that 4chan will not be back because the Trump glowniggers do not control 4chan. The Trump admin will not allow it. Simple as.
[Read more] >it's a total kike victory if 4chan remains down
>hacking 4chan is them wanting to put an end to twitter/redditors getting red pilled from visiting /pol/, and further spreading the anti-semitism diease on their normiespheres
No one in the past 8 years has been getting red pilled from visiting /pol/ but they have been psyopped. The true reason why 4chan went down is because they lost their funding. They even made an april fool's joke out of it. Since 2016, 4chan survived off federal gibs (but through unofficial channels). Hence why gookmoot has been so silent ever since Trump was meme'd into office: the old US elites were pretty pissed. But he needed money to keep 4chan alive and he probably figured it was in his best interest to take a deal from US glowniggers.
In 2020 Trump lost because dems cheated. The amount of internet censorship at this time was insane. Even on 4pol you could get moderated talking about it, not consistently, but still. But to talk about the steal on normieplatforms? Impossible. And mind you, I'm not even American, I'm a Eurofag. My theory is that they first needed 4 more years of Biden to start to Ukraine war and lay the groundwork for that conflict. But after that, they would let Trump in again and crash the global economy. So far... based off of the chaos we're seeing, I think my theory holds.
But the point I'm trying to make is this: 4chan is owned by gookmoot who is not under the thumb of the pro Trump glowniggers. So that's why they simply terminated it. And they were pretty open about it: see picrel. The satanic glownigger faction knew that 4chan would be terminated at some point and that's why donkey show exists: it's the fallback base. So when they pulled the plug at 4chan, they made a nice little story about a hack. The media shilled the soyjak URL and the 4chan userbase migrated there. Go on donkey showpol right now and if you cannot unsee the similarity with 4pol.
I guarantee you that 4chan will not be back because the Trump glowniggers do not control 4chan. The Trump admin will not allow it. Simple as.
>>386502
When did it get filtered? Is mlpol on bad terms with the soyjaks?
I honestly don't got any ill well or hate for the /qa/ refugees.
It was fun raiding /qa/ back in the day, I sure miss them.
When did it get filtered? Is mlpol on bad terms with the soyjaks?
I honestly don't got any ill well or hate for the /qa/ refugees.
It was fun raiding /qa/ back in the day, I sure miss them.
>>386510
I mean, donkey show is rather responsible for us all being digital refugees and if this thread is accurate they're trying to hack anyone who tries to post on their website.
I mean, donkey show is rather responsible for us all being digital refugees and if this thread is accurate they're trying to hack anyone who tries to post on their website.
>>386510
I liked /qa/ too but even back then it was really an aquired taste. A lot of people used to hate it from the get-go because the original purpose of soijaks was as an extremely low-effort ad hominem response originating from /v/ and /pol/ and contributing zero to the discussion, and so dismissed /qa/ outright. A lot of other people just hate the style: aesthetically speaking, jaks are not made to be particularly appealing. /qa/ was also never really a place to have serious discussions; I had a friend who called it a "postmodern [s4s]", which I think is about accurate, and understandably that's not everyone's cup of tea.
The 'arty has made things worse because they've embraced the "evil shitposter counterculture" image and made spamming and raiding core parts of their culture. They've raided /mlpol/ in the past from what I'm aware. They've also had endless involvement with CP raids, discord grooming cults and all other kinds of bottom of the barrel cesspits - not necessarily guilty of it themselves but still existing in the same filthy spheres of the internet. Like the other anon says the site itself is shady and not above executing obfuscated JS and running port scans.
I still think the evolving nature of jakking is interesting to watch from the sidelines, but nowadays actually posting there is not very pleasant and I never really migrated after /qa/ was killed. Kway was fun shitposting, the party is malicious, weaponised shitposting. So I can very well understand how people who never even liked /qa/ in the first place would hate the party.
[Read more] I liked /qa/ too but even back then it was really an aquired taste. A lot of people used to hate it from the get-go because the original purpose of soijaks was as an extremely low-effort ad hominem response originating from /v/ and /pol/ and contributing zero to the discussion, and so dismissed /qa/ outright. A lot of other people just hate the style: aesthetically speaking, jaks are not made to be particularly appealing. /qa/ was also never really a place to have serious discussions; I had a friend who called it a "postmodern [s4s]", which I think is about accurate, and understandably that's not everyone's cup of tea.
The 'arty has made things worse because they've embraced the "evil shitposter counterculture" image and made spamming and raiding core parts of their culture. They've raided /mlpol/ in the past from what I'm aware. They've also had endless involvement with CP raids, discord grooming cults and all other kinds of bottom of the barrel cesspits - not necessarily guilty of it themselves but still existing in the same filthy spheres of the internet. Like the other anon says the site itself is shady and not above executing obfuscated JS and running port scans.
I still think the evolving nature of jakking is interesting to watch from the sidelines, but nowadays actually posting there is not very pleasant and I never really migrated after /qa/ was killed. Kway was fun shitposting, the party is malicious, weaponised shitposting. So I can very well understand how people who never even liked /qa/ in the first place would hate the party.
>>386515
Well damn. It's really is a donkey show.
I guess I'll write them off, because it sound like they went off the deep end
Well damn. It's really is a donkey show.
I guess I'll write them off, because it sound like they went off the deep end
>>386520
>I guess I'll write them off, because it sound like they went off the deep end
you could say that
>I guess I'll write them off, because it sound like they went off the deep end
you could say that
>>386513
honestly i dont see the problem with them emberassing the mods of 4chuck even if its fake and gay (not actually the soyteens). its more a matter of please celestia let that happen because it would be so fucking funny that mods on 4chan got pwned by retards.
honestly i dont see the problem with them emberassing the mods of 4chuck even if its fake and gay (not actually the soyteens). its more a matter of please celestia let that happen because it would be so fucking funny that mods on 4chan got pwned by retards.
>>386515
>The 'arty has made things worse because they've embraced the "evil shitposter counterculture" image and made spamming and raiding core parts of their culture.
I hated /b/ but seeing this makes me think they where right and people like this should have been gate kept.
>The 'arty has made things worse because they've embraced the "evil shitposter counterculture" image and made spamming and raiding core parts of their culture.
I hated /b/ but seeing this makes me think they where right and people like this should have been gate kept.
>>386537
>Do you actually believe a company that pays 50 000 - 200 000 dollars every month in server costs has a vulnerability like that?
Maybe they should had shoveled that amount into software development so they wouldn't had codebase with decade old components with decade old vulnerabilities.
>Do you actually believe a company that pays 50 000 - 200 000 dollars every month in server costs has a vulnerability like that?
Maybe they should had shoveled that amount into software development so they wouldn't had codebase with decade old components with decade old vulnerabilities.
[Reply] [Last 50 Posts] [Last 100 Posts] [Last 200 Posts]
You are viewing older replies. Click [View All] or [Last n Posts] to vew latest posts.
Clicking update will load all posts posted after last post on this page.
Post pagination: [Prev] [1-100] [101-200] [201-221] [Next] [Live (last 100 replies)]
221 replies | 54 files | 80 UUIDs | Page 8
[Add to Thread Watcher]










 Ex: Type :littlepip: to add Littlepip
Ex: Type :littlepip: to add Littlepip  Ex: Type :eqg-rarity: to add EqG Rarity
Ex: Type :eqg-rarity: to add EqG Rarity 