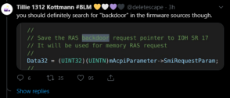
See the title. We should totally use this newly revived board to spark interest in the deep web, alternative tech, etc., just like what had happened around a year ago with archiving and DIY. At work right now but I'm gonna be downloading TOR onto this laptop and spending a bit exploring.
I wouldn't advocate for illegal activity, but just post whatever interests you or you think would be fun to visit as a board. I bet we could shake a forum or two up at the very least, eh?
/cyb/ - Cyberpunk Fiction and Fact
Cyberpunk is the idea that technology will condemn us to a future of totalitarian nightmares here you can discuss recent events and how technology has been used to facilitate greater control by the elites, or works of fiction
22 replies | 18 files | 12 UUIDs | Page 9
>>884
Well you could still use Cyberghost or another VPN service to post here, or just, use another device like your phone while exploring on your main device.
Well you could still use Cyberghost or another VPN service to post here, or just, use another device like your phone while exploring on your main device.
Sorry for abandoning. Lots of life stuff, a fresh new bottle of whiskey, and a few other home modifications kept me away. So far I have a few sites relevant to our interests, mostly chans and forums.
http://nanochanxv2lxnqi.onion
NanoChan is a similar place to regular 4chan. It's got a /g/, /v/, /a/, /pol/, /b/, and a /meta/ for discussion of deepweb and chan topics.
http://76qugh5bey5gum7l.onion/
A nice place to listen to musics while browsing. I like Deep Banjo, Anonny Jazz, Deep Space One, Groove Salad, and C0vertElectro.
http://hackerw6dcplg3ej.onion/
Er...I don't know exactly what's wrong but on my end I get an infinite string of "anti-flood" captcha prompts. Not sure if the site's broken and the books on hacking/opsec are gone, or if this is a test of some kind. If anyone else gets in, let me know because I would love to learn the way of the grey hat/white hat.
http://inclibuql666c5c4.onion/
A collection of politically incorrect literature in a load of languages. From what I hear on the grapevine, there's over a thousand natsoc works. Pretty noice find, eh?
http://answerszuvs3gg2l64e6hmnryudl5zgrmwm3vh65hzszdghblddvfiqd.onion/
A Yahoo Answers style site on the Tor service, in case you want to flood them with newbie questions lmao
Sidenote: if you want to sign up for a forum or site like the above, use an anonymous email service. No GMail or Yahoo or AOL. ProtonMail is a good start, but I personally prefer cock.li, SIGAINT, VFEMail, or Lelantos. Each of them are easy enough to find for yourself using DuckDuckGo. Just remember that without personal encryption keys and such, you are at the whims of the email provider, who could be anything from an FBI agent to a scammer to a NordVPN style snake who's willing to sell or give away your metadata. Trust no one until you are certain of their efficacy.
A sidenote: using a VPN on top of Tor is both a good and bad thing, depending on the number of people using both. For instance, let's say 20,000 people use ExpressVPN and 100,000 use Tor at the same time, but the overlap is only a few dozen. That narrows the search for a prospecting narc to hunt your IP down to a few hours of checking sites you frequent using these services.
Anyone else been exploring, or am I alone here? Guessing the latter but hopefully not.
http://nanochanxv2lxnqi.onion
NanoChan is a similar place to regular 4chan. It's got a /g/, /v/, /a/, /pol/, /b/, and a /meta/ for discussion of deepweb and chan topics.
http://76qugh5bey5gum7l.onion/
A nice place to listen to musics while browsing. I like Deep Banjo, Anonny Jazz, Deep Space One, Groove Salad, and C0vertElectro.
http://hackerw6dcplg3ej.onion/
Er...I don't know exactly what's wrong but on my end I get an infinite string of "anti-flood" captcha prompts. Not sure if the site's broken and the books on hacking/opsec are gone, or if this is a test of some kind. If anyone else gets in, let me know because I would love to learn the way of the grey hat/white hat.
http://inclibuql666c5c4.onion/
A collection of politically incorrect literature in a load of languages. From what I hear on the grapevine, there's over a thousand natsoc works. Pretty noice find, eh?
http://answerszuvs3gg2l64e6hmnryudl5zgrmwm3vh65hzszdghblddvfiqd.onion/
A Yahoo Answers style site on the Tor service, in case you want to flood them with newbie questions lmao
Sidenote: if you want to sign up for a forum or site like the above, use an anonymous email service. No GMail or Yahoo or AOL. ProtonMail is a good start, but I personally prefer cock.li, SIGAINT, VFEMail, or Lelantos. Each of them are easy enough to find for yourself using DuckDuckGo. Just remember that without personal encryption keys and such, you are at the whims of the email provider, who could be anything from an FBI agent to a scammer to a NordVPN style snake who's willing to sell or give away your metadata. Trust no one until you are certain of their efficacy.
A sidenote: using a VPN on top of Tor is both a good and bad thing, depending on the number of people using both. For instance, let's say 20,000 people use ExpressVPN and 100,000 use Tor at the same time, but the overlap is only a few dozen. That narrows the search for a prospecting narc to hunt your IP down to a few hours of checking sites you frequent using these services.
Anyone else been exploring, or am I alone here? Guessing the latter but hopefully not.
Anonymous
No.889
>>888
I've used Brave and it's alright. I just use plain Tor Browser since I am more experienced with that and I can rest assured of its general security. I can't guarantee anything with Brave other than a tolerable anti-spam advertisement model and nice UI.
I've used Brave and it's alright. I just use plain Tor Browser since I am more experienced with that and I can rest assured of its general security. I can't guarantee anything with Brave other than a tolerable anti-spam advertisement model and nice UI.
Anonymous
No.890
I recently found out that Brave just added that as a way of using .onion domains on Brave. As good as Brave is, it's not as secure as Tor. And hell, even Tor isn't so safe since there are small zero-days and issues with security if you're using specific sites regularly enough to be tracked.
I never really trusted TOR and its "untracability", but considering not everyone is a part of the bog gov't, that can be more than enough for guaranteeing an user's anonymity.
Anecdotal, sure but I spent a while wondering "How" recently.
If you think you're safe using TOR browser, posting or finding info or dissident stuff, evading some bans, having different accounts for whatever reason and not getting them linked or because your DSL comes with a static IP and now browsers and OSes are like sponges that will get you identified, hacking or anything, remain skeptic.
Elite proxies and other things like that are a thing of the past. Only good to maybe override a regional block on some shit site. For most websites you should be fine with TOR, or I believe so. But I never expected that from a site we know well, one of the admins knew how to do it. And he did it!
No name will be given but I had a chat with him, either you're bluffing, either you're skilled, and well if you let me know that, you're based.
Imagine, I make a trolling account on a /pol/ forum. Register the email adress from a proxy in Germany on a PC I just connected on the internet. My network of course, behind a NAT router blocking what should be blocked.
It's running LinuxMint 19 64bit, XFCE, all up-to-date, apt-get the TOR package and all run smoothly, last version installed, and I think it's safe, let's try this out, since my customer wanted something safe.
>Shitpost in the aforementioned horse-politics forum, and the next day, get caught. «samefag!»
With hundred of users on this place at once, it can't be a wild guess, and go through a long process of repeating the experiment, finding what leaked.
2017 already there was a secu fault since a simple file:// could identify your machine. Even with a minimal lot of scripts loaded I wonder how this could have been possible. I repeated the process checking what most can do, with nothing relevant so far.
I'm not bragging anywhere, not on IRC or Discord about that troll account or even suggested its existence, which would leak. My wildest guess would be on the metadata from uploading an avatar for my guy, that could carry a signature of some kind, but that again is unlikely.
TBH, It was worth being banned from that site for this, afteall it's just a game but gets intresting.
Of course the admin could have lied and said ( On IRC, which I jumped in immediately, to claim my purity and play the poor innocent guy)
«Just kidding, I trolled you, it was random and indeed without proof, should've lift the ban you can move on, don't pay attention keep posting!» while not telling me he knew it was me. Or
«I recognized your style and punctuation and based a wild guess and baited you to admit and it worked.»
which would be a bold assume, and doesn't ressembles the guy, but since he mentioned cash,
«I know You're this Mote guy shitposting as that antifa on crack using TOR.»
And evasively hinted that yes, he made it. He tracked my original IP or managed to identify me over TOR, noscript, but this guy knows an exploit or security fault, and of course, he's using it.
Of course it's my abuse of trust, even small - wouldn't leak anything huge without at least using a throwaway phone with a free demo sim card with a few megs of data. But I could have used a random phone, or dumpster laptop on gentoo in a public wifi, a café, supermarket's or even spoofing my location.
Because even if you jump on the neighbor's wifi, a simple peek at the whois will reveal your location, and now on a small city, that's just begging for the wild guess/intuition, You should appear really at two different locations - home, no proxy or anything weird - and your troll, far away from there. Which you can get done with Tor.
You should NOT trust something that pretends to be safe, even with SSL and noscript, and a few stuff.
So far, after rechecking everything, my wild guess would be
- I use a rather odd resolution ( 1920x1200 )
- TOR, now even maximized puts a border to reduce the workspace to a certain fake resolution, like it's a security measure that given it out, instead of suggesting a common 1920x1080 resolution.
- It does keeps the aspect ratio, a simple rule of three reveals the native resolution and hints enough on the browser to link an user to another.
- Something else.
Anecdotal, sure but I spent a while wondering "How" recently.
If you think you're safe using TOR browser, posting or finding info or dissident stuff, evading some bans, having different accounts for whatever reason and not getting them linked or because your DSL comes with a static IP and now browsers and OSes are like sponges that will get you identified, hacking or anything, remain skeptic.
Elite proxies and other things like that are a thing of the past. Only good to maybe override a regional block on some shit site. For most websites you should be fine with TOR, or I believe so. But I never expected that from a site we know well, one of the admins knew how to do it. And he did it!
No name will be given but I had a chat with him, either you're bluffing, either you're skilled, and well if you let me know that, you're based.
Imagine, I make a trolling account on a /pol/ forum. Register the email adress from a proxy in Germany on a PC I just connected on the internet. My network of course, behind a NAT router blocking what should be blocked.
It's running LinuxMint 19 64bit, XFCE, all up-to-date, apt-get the TOR package and all run smoothly, last version installed, and I think it's safe, let's try this out, since my customer wanted something safe.
>Shitpost in the aforementioned horse-politics forum, and the next day, get caught. «samefag!»
With hundred of users on this place at once, it can't be a wild guess, and go through a long process of repeating the experiment, finding what leaked.
2017 already there was a secu fault since a simple file:// could identify your machine. Even with a minimal lot of scripts loaded I wonder how this could have been possible. I repeated the process checking what most can do, with nothing relevant so far.
I'm not bragging anywhere, not on IRC or Discord about that troll account or even suggested its existence, which would leak. My wildest guess would be on the metadata from uploading an avatar for my guy, that could carry a signature of some kind, but that again is unlikely.
TBH, It was worth being banned from that site for this, afteall it's just a game but gets intresting.
Of course the admin could have lied and said ( On IRC, which I jumped in immediately, to claim my purity and play the poor innocent guy)
«Just kidding, I trolled you, it was random and indeed without proof, should've lift the ban you can move on, don't pay attention keep posting!» while not telling me he knew it was me. Or
«I recognized your style and punctuation and based a wild guess and baited you to admit and it worked.»
which would be a bold assume, and doesn't ressembles the guy, but since he mentioned cash,
«I know You're this Mote guy shitposting as that antifa on crack using TOR.»
And evasively hinted that yes, he made it. He tracked my original IP or managed to identify me over TOR, noscript, but this guy knows an exploit or security fault, and of course, he's using it.
Of course it's my abuse of trust, even small - wouldn't leak anything huge without at least using a throwaway phone with a free demo sim card with a few megs of data. But I could have used a random phone, or dumpster laptop on gentoo in a public wifi, a café, supermarket's or even spoofing my location.
Because even if you jump on the neighbor's wifi, a simple peek at the whois will reveal your location, and now on a small city, that's just begging for the wild guess/intuition, You should appear really at two different locations - home, no proxy or anything weird - and your troll, far away from there. Which you can get done with Tor.
You should NOT trust something that pretends to be safe, even with SSL and noscript, and a few stuff.
So far, after rechecking everything, my wild guess would be
- I use a rather odd resolution ( 1920x1200 )
- TOR, now even maximized puts a border to reduce the workspace to a certain fake resolution, like it's a security measure that given it out, instead of suggesting a common 1920x1080 resolution.
- It does keeps the aspect ratio, a simple rule of three reveals the native resolution and hints enough on the browser to link an user to another.
- Something else.
Anonymous
No.1149

1598811029_3.webm (964.1 KB, Resolution:1120x720 Length:00:00:08, 1598810939.webm) [play once] [loop]
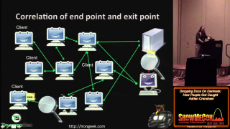
>>885
I wouldn't trust a VPN. Just setup your own proxy or use Tor.
>>888
>TOR add-on.
never use any Tor addons or "tor tabs" always use...
1) Tor Browser (better because it doesn't have the same fingerprint as your main browser. also, set your security level to safer/safest in Tor Browser settings. Do not use any tripcodes, names or avatars AND always clear the meta-data from all files that you upload!)
Protip: if you use Linux, you can use https://github.com/micahflee/torbrowser-launcher to securely download and verify Tor Browser
2) Install plain tor and configure it manually as proxy or use torsocks (read https://wiki.archlinux.org/index.php/Tor for more info)
3) Use Tails (safest)
I wouldn't trust a VPN. Just setup your own proxy or use Tor.
>>888
>TOR add-on.
never use any Tor addons or "tor tabs" always use...
1) Tor Browser (better because it doesn't have the same fingerprint as your main browser. also, set your security level to safer/safest in Tor Browser settings. Do not use any tripcodes, names or avatars AND always clear the meta-data from all files that you upload!)
Protip: if you use Linux, you can use https://github.com/micahflee/torbrowser-launcher to securely download and verify Tor Browser
2) Install plain tor and configure it manually as proxy or use torsocks (read https://wiki.archlinux.org/index.php/Tor for more info)
3) Use Tails (safest)
There are also other anonymity networks such as I2P, GNUnet and Freenet (out of these I2P is the best, IMO)
1602784461_1.png (450.2 KB, 1366x768, Screenshot_20201015_135305.png)
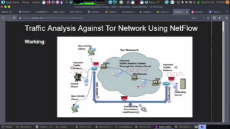
1602784461_2.png (436.1 KB, 1366x768, Screenshot_20201015_135354.png)
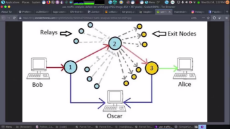
>HOW JOURNALISTS/TOR USERS ARE TRACKED FROM PIXELS TO PACKET INJECTION/ANALYSIS OF NODE PATH
>If you aren't using best practices, those at higher risk need for targeting (ie: journalists under dictatorship) to pay special attention to how they use Tor with other tools (best practices): Covering Traffic analysis from pixel storage to tracking by packet injection analysis, zombie/super cookies and persistent identifiers to name a few...
https://www.youtube.com/watch?v=QHK6RYPoVTo
Mirror: https://www.bitchute.com/video/qAgUDBKWNwqn/
>If you aren't using best practices, those at higher risk need for targeting (ie: journalists under dictatorship) to pay special attention to how they use Tor with other tools (best practices): Covering Traffic analysis from pixel storage to tracking by packet injection analysis, zombie/super cookies and persistent identifiers to name a few...
https://www.youtube.com/watch?v=QHK6RYPoVTo
Mirror: https://www.bitchute.com/video/qAgUDBKWNwqn/
Anonymous
No.1204
>>1039
Hello, I think I can probably find the issue you're talking about. Can you direct me to the forum in question?
Hello, I think I can probably find the issue you're talking about. Can you direct me to the forum in question?
>>1173
Very interesting, but the first picture seems to imply a targeted attack and the second implies using an exit node. The attack on the first pic might also need one. If Tor is being used to access hidden services, this problem becomes much smaller.
Very interesting, but the first picture seems to imply a targeted attack and the second implies using an exit node. The attack on the first pic might also need one. If Tor is being used to access hidden services, this problem becomes much smaller.
>>1212
More TOR vulnerabilities:
>Can You be Deanonymized on TOR?
>Is TOR Safe? This video talks about 6 flaws of TOR and to see if these flaws affect you and your privacy. Can TOR be decrypted by 3 Letter agencies?
>Watch the conclusion at the end of the video.
https://www.youtube.com/watch?v=UJ_iUWG-kEs
More TOR vulnerabilities:
>Can You be Deanonymized on TOR?
>Is TOR Safe? This video talks about 6 flaws of TOR and to see if these flaws affect you and your privacy. Can TOR be decrypted by 3 Letter agencies?
>Watch the conclusion at the end of the video.
https://www.youtube.com/watch?v=UJ_iUWG-kEs
1612678131.webm (15.4 MB, Resolution:528x432 Length:00:13:29, can-you-be-deanonymized-on-tor_--rob_braxman-tech.webm) [play once] [loop]

>>1265
>yewtu.be
Not sure how legit is that site, it looks like a clone of the proper INVIDIOUS.
By the way, the link of this video in indivious is https://invidious.site/watch?v=rSmGxw0GSq8
Perhaps some anon can vouch for YEWTU.
>yewtu.be
Not sure how legit is that site, it looks like a clone of the proper INVIDIOUS.
By the way, the link of this video in indivious is https://invidious.site/watch?v=rSmGxw0GSq8
Perhaps some anon can vouch for YEWTU.
Anonymous
No.1267
>>1265
Thanks anon. Watching now.
The jewtube link just in case:
https://www.youtube.com/watch?v=rSmGxw0GSq8
Thanks anon. Watching now.
The jewtube link just in case:
https://www.youtube.com/watch?v=rSmGxw0GSq8
>>1266
There is no 'proper' invidious, like there is no proper nitter, and no proper bibliogram. The projects are open source to encourage more hosts to maintain their own instances, and make them known to the wider public so that the load can be better distributed across them.
There is no 'proper' invidious, like there is no proper nitter, and no proper bibliogram. The projects are open source to encourage more hosts to maintain their own instances, and make them known to the wider public so that the load can be better distributed across them.
>>1269
>>1268
>>1266
There is a proper Invidous, https://invidio.us, but the guy got bored of it so now it just redirects to other hosts. It's useful for looking for a working instance, since they all occasionally break.
>>1268
>>1266
There is a proper Invidous, https://invidio.us, but the guy got bored of it so now it just redirects to other hosts. It's useful for looking for a working instance, since they all occasionally break.
Anonymous
No.1275
>>1270
The invidious site that was managed by the original developer was just another instance. It's no longer maintained as such, and now just points to other instances. There is no invidious proper, and there never was, just instances.
The invidious site that was managed by the original developer was just another instance. It's no longer maintained as such, and now just points to other instances. There is no invidious proper, and there never was, just instances.
Anonymous
No.1281
>Dropping Docs On Darknets How People Got Caught Adrian Crenshaw
>Tor
https://www.youtube.com/watch?v=28dOllHyoM0
Mirror: https://www.bitchute.com/video/H10Rsh1x9Foo/
>Tor
https://www.youtube.com/watch?v=28dOllHyoM0
Mirror: https://www.bitchute.com/video/H10Rsh1x9Foo/